It is basically common place now - phishing - when 'unsavoury' individuals are trying to get something from you using less than honest approach over the internet. There really is no way to immunize yourself, but if you can get really good at spotting their 'lures' you'll be very hard to catch and basically immune anyways.
I got a really spectacular one today, and one a few weeks ago, so it prompted me to write about it. I know it's not very 'photo & art' as my blog would suggest, but as photographers we spend a lot of time online, with a lot of our assets online, so I think because its about protecting those assets - it's still relevant.
Read on if you want to see some tips to protect yourself and help solve the problems they create.
First, there are a lot of ways that people can phish for information online. Most of the time it arrives via email.
The first step to keeping a secured email inbox is by using an email client. I use regular old Apple Mail to grab email from a few different inboxes online (my domain one, my hotmail one I've had since a teenager, etc). Email client software is great for a few reasons, firstly ; you can have all your previous messages saved on your computer, so even if you're not connected to the internet, you can still get the information, and you can collect all your email in one spot instead of visiting three places if you have three different inboxes.
The other great thing is that they have some great features to help keep you secured. One of those features is they can be set to not load images automatically which believe it or not is a great privacy feature ; certain senders will attach a unique image to each email they send out, and when you open your email, that image loads, and now they know "hey, Jane Doe's unique image was just opened at 3pm today, we know if/when she has checked her message from us". Thats not so much to do with phishing but its good nonetheless.
They can show you a messages 'true' sender a little better than an online client does. Take for instance, PayPal. I got a phishing scam from paypal a few months ago, or at least it appeared to be from them. All I have to do to see the true sender is hover over the address and even though they changed their 'sender's name' to "PayPal" I could see it was coming from some random.ru Russian domain name, and thus, not the legit PayPal. The fastest and easiest way is to check who the sending domain name is - Royal Bank of Canada is never going to send you an email from any other domain address other than their home one, 'rbcroyalbank'
Next, if the email address doesn't have you doubting, spot poor grammar. Improper capitalizations, blatant misspellings, inconsistent punctuation, repeated and redundant lines, or just generally vague text are all great signs. Here's today's message:
Well the easy and obvious next step is to delete the message. But if you want to prevent, other, perhaps more oblivious individuals from being phished, you should do this as well;
Use your email client to hover over (not click) the link they are pointing you to. In this case it was lou-castelveil.fr and within a subdomain of it the hackers would have injected their malware. In a lot of cases, the owner of the original domain name isn't to blame, or guilty of any wrong doings. And a lot of times, they may be totally oblivious that their site is being used to host malware or phishing schemes. So I visited lou-castelveil.fr, its a restaurant in Paris as I found out and I contacted them to inform them that their website is being used for phishing or malware scams. I didn't share the exact link that the scam was pointing to, instead I told them which sub folders they would find it in. All they need to do is have their webmaster go into their domain directory, find the files that they didn't put there, delete them and change their passwords. It's not much, but that would be the ideal next step, contact the legitimate website owner and bring them into the loop.
Recently, about a month ago, my real estate agent's co-worker was hacked. The coworker sent out a bunch of spam emails to a large list of people. It pointed to a phishing or malware scheme on some "Women's Day organization something or other". Again, I messaged the legitimate site owner to have their web master jump on the issue. The other side of the problem was; the coworker shared the same image signature for the brokerage as my agent had in her emails. Because her coworker sent spam, the internet community identified and reported it as spam, and now that 'image signature for the brokerage' had essentially a black flag, and my email server was bouncing back every (legit) message my agent was trying to send me. You could imagine the frustration when my agent had important emails to send us that we couldn't receive.
I got a really spectacular one today, and one a few weeks ago, so it prompted me to write about it. I know it's not very 'photo & art' as my blog would suggest, but as photographers we spend a lot of time online, with a lot of our assets online, so I think because its about protecting those assets - it's still relevant.
Read on if you want to see some tips to protect yourself and help solve the problems they create.
The Symptoms to Help You Spot a Phishing Scam
 |
| An example of a really poorly designed scam email. |
First, there are a lot of ways that people can phish for information online. Most of the time it arrives via email.
The first step to keeping a secured email inbox is by using an email client. I use regular old Apple Mail to grab email from a few different inboxes online (my domain one, my hotmail one I've had since a teenager, etc). Email client software is great for a few reasons, firstly ; you can have all your previous messages saved on your computer, so even if you're not connected to the internet, you can still get the information, and you can collect all your email in one spot instead of visiting three places if you have three different inboxes.
The other great thing is that they have some great features to help keep you secured. One of those features is they can be set to not load images automatically which believe it or not is a great privacy feature ; certain senders will attach a unique image to each email they send out, and when you open your email, that image loads, and now they know "hey, Jane Doe's unique image was just opened at 3pm today, we know if/when she has checked her message from us". Thats not so much to do with phishing but its good nonetheless.
They can show you a messages 'true' sender a little better than an online client does. Take for instance, PayPal. I got a phishing scam from paypal a few months ago, or at least it appeared to be from them. All I have to do to see the true sender is hover over the address and even though they changed their 'sender's name' to "PayPal" I could see it was coming from some random.ru Russian domain name, and thus, not the legit PayPal. The fastest and easiest way is to check who the sending domain name is - Royal Bank of Canada is never going to send you an email from any other domain address other than their home one, 'rbcroyalbank'
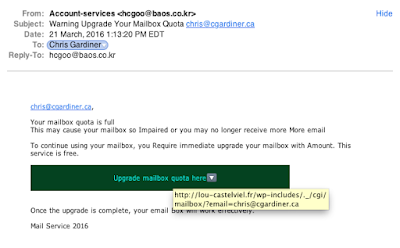
Next, if the email address doesn't have you doubting, spot poor grammar. Improper capitalizations, blatant misspellings, inconsistent punctuation, repeated and redundant lines, or just generally vague text are all great signs. Here's today's message:
Your mailbox quota is full
This may cause your mailbox so Impaired or you may no longer receive more More email
To continue using your mailbox, you Require immediate upgrade your mailbox with Amount. This service is free. [Then They Had a Link Button Here]
Once the upgrade is complete, your email Box will work effectively.In this case, they don't even know who my email domain is. I can tell you, its definitely not "Mail Service 2016".
Mail Service 2016
What Should You Do Next
Well the easy and obvious next step is to delete the message. But if you want to prevent, other, perhaps more oblivious individuals from being phished, you should do this as well;
Use your email client to hover over (not click) the link they are pointing you to. In this case it was lou-castelveil.fr and within a subdomain of it the hackers would have injected their malware. In a lot of cases, the owner of the original domain name isn't to blame, or guilty of any wrong doings. And a lot of times, they may be totally oblivious that their site is being used to host malware or phishing schemes. So I visited lou-castelveil.fr, its a restaurant in Paris as I found out and I contacted them to inform them that their website is being used for phishing or malware scams. I didn't share the exact link that the scam was pointing to, instead I told them which sub folders they would find it in. All they need to do is have their webmaster go into their domain directory, find the files that they didn't put there, delete them and change their passwords. It's not much, but that would be the ideal next step, contact the legitimate website owner and bring them into the loop.
Recently, about a month ago, my real estate agent's co-worker was hacked. The coworker sent out a bunch of spam emails to a large list of people. It pointed to a phishing or malware scheme on some "Women's Day organization something or other". Again, I messaged the legitimate site owner to have their web master jump on the issue. The other side of the problem was; the coworker shared the same image signature for the brokerage as my agent had in her emails. Because her coworker sent spam, the internet community identified and reported it as spam, and now that 'image signature for the brokerage' had essentially a black flag, and my email server was bouncing back every (legit) message my agent was trying to send me. You could imagine the frustration when my agent had important emails to send us that we couldn't receive.
Spot Malware on Your Own Domain
I've actually found malware on both; my own domain www.cgardiner.ca and a website I was recently contracted to design. Well I don't know if it was malware, but I certainly didn't put it there. Here is how I found it in both cases;
On My Own Site;
It had been so long since I updated it, that I was trying to compare the files on the remote site (aka accessible to the internet) and the files on my local site (aka the ones I design with on my computer while offline, that aren't accessible to the internet) and I saw that some were more recently modified than the most recent changes I upload. So if the last time I changed my site was November 2014, why did I see changes on the public version in May of 2015? Someone else had to make those changes - not me. So the only way I knew to fix it was to remove the modified files and directories, update with the ones from my local computer, and change the password to access the domain directories. Thats it. Spotting it was really as simple as clicking on 'sort by recently modified' which you can find on just about every single file structure there is.
On a Client Site:
I was going through their existing version that was publicly accessible, and because I was gathering all the info I needed to copy into my new design format, I had to visit every single page they already had in existence. Then I found some pages appeared to be there, but weren't. And instead of the pages that were supposed to be there, they were replaced with these 'malware portals' I will call them, that led to somewhere else than they were supposed to. In this case, I wasn't the original designer of the page, so I didn't have copies of what was supposed to be there. We had to just remove the faulty sections and I had to hurry up and get my safer version online.
Anyways, not my most interesting, or visually engaging read, but hopefully it helps someone out there to avoid falling victim to these internet trolls.